CartellaUnicaTasse.exe An Italian Malware Reverse
Transcript
CartellaUnicaTasse.exe An Italian Malware Reverse
CartellaUnicaTasse.exe An Italian Malware Reverse Engineering
Study
Author: Giuseppe Bonfa' ALIAS Evilcry
E-Mail: evilcry (AT) gmail (DOT) com
Website: http://evilcry.altervista.org
Blog: http://evilcodecave.wordpress.com
The Essay
CartellaUnicaTasse.exe is an e-mail spreaded Malware that acts as a Downloader
Agent for other Malicious Executable Applications. Thanks to CUT.exe a series of
executables are downloaded and runned into the victim user.
In this paper we will analyze with a classical RCE Approach the entire structure
of CartellaUnicaTasse from the pure Infection to the Network Point of View.
The first executable is delivered as a normal mail attachment with subject
Cartella esattoriale n° 003 210400360968173, and its written in VB6 with a layer
of UPX, so after a first detection became really easy to detect it.
CartellaUnicaTasse basically attempts to enstablish a connection with
http://2mug.biz/mef/ and after accessing it, executes the downloaded
applications.
This is the list of downloaded executables:
[DIR] Parent Directory
download1.exe
10-Jun-2008 08:32
download1.exe_DAMM 16-Jun-2008 07:29
download2.exe
10-Apr-2008 03:59
download3.exe
10-Apr-2008 04:04
loader_mef.exe
13-Jun-2008 09:07
mef.exe
10-Jun-2008 08:32
mef.exe_old
19-May-2008 15:24
Download1.exe
Name: Download1.exe
MD5: 457B534D1141F8B70548506D0D83B4C0
SHA-1: 5D9E106F4B8684D56EF67EB744FCF7CC24B1A23C
Download1.exe works as dialer and is truly similar to Mef.exe, evidently the
coder spreaded two versions, download1.exe included into the dowloader
CartellaUnicaTasse, and mef that is only placed into 2mug.biz/mef/ directory.
Download2.exe
Name: Download2.exe
MD5: 93790593E3B95D6E9CE1EF055FEE2D0E
SHA-1: 1314F59CB1469D67AD4566611BB2972CB9C8764F
Download2.exe is packed with NSPack, it's easy to unpack it, just watch IDA
Graph to locate the last instruction of the graph, this will be jump for the
OEP.
Also Download2.exe acts as a dialer, and in the same time generates a copy of
itself into \system32\ directory.
Let's see in detail what it does:
RegOpenKeyExA (HKLM\System\CurrentControlSet\Services\Winsock2\Parameters)
RegOpenKeyExA (HKLM\SOFTWARE\Microsoft\CTF\Compatibility\dwnld2_unpacked.exe)
RegOpenKeyExA
(HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellCompatibility\Applications\
dwnld2_unpacked.exe)
RegOpenKeyExA
(HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellCompatibility\Objects\
{20D04FE0-3AEA-1069-A2D8-08002B30309D})
RegOpenKeyExA (HKCR\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D}\InProcServer32)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\2mug.biz\,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\2mug.biz\www,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\2mug.biz\www,REG_DWORD)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\Zones\2,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\Zones\2,REG_DWORD)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\928476362.com\,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\928476362.com\www,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\928476362.com\www,REG_DWORD)
There is a little difference between this dialer and the others, Download1,
Download3 and Mef.exe acts uniquely with 2mug.biz, Download2 inserts into the
ZoneMap also 928476362.com.
Download2 creates also a copy of itself placed in C:\WINDOWS\System32\dllconfig\
cache\dllcache.exe
The directory System32\dllconfig\cache\ does not exists as System Directory and
is created at runtime by the dialer, with a name that remembers
System32\dllcache, that's a Real System Directory.
00401B2C call
sub_4015A0 contains intersting informations, inside this call
we can see intersting strings:
hxxp://mygalleries.biz
/mail.php
and an HTTP Header:
POST %s HTTP/1.0',0Dh,0Ah
Host: %s
Content-type: application/x-www-form-urlencoded
Content-length: %d
after opening a socket, is called GetHostByName with argument hxxp://googlehard.com and some Network operation is accomplished. This malware is not an
intersting one :)
Download3.exe Trojan-Downloader.Win32.VB.fcd
Name: Download3.exe
MD5: 63AC4A54790D71AB99FC050E5D3B4F5A
SHA-1: 61F293926800926722866A72B9EA3DE9522600FB
This executable is basically packed with UPX, and does not exist any problem in
unpacking it. The structure of the code is really and easy, with
SHGetSpecialFolderPathA is located the SpecialFolder of the current account that
is running the executable.
Usually C:\Documents and Settings\_UserName_\Application Data\
Next a set of splitted strings are composed:
disinstalla.htm
syslcznp.exe
C:\Documents and Settings\_UserName_\Application Data\semanatiba\syslcznp.exe
The content of syslcznp.exe is loaded from the internal resources of download3
and next builded with CreateFile and WriteFile.
As all others malicious executables cooming from the same source (Download1.exe,
Download2.exe, loader_mef.exe, mef.exe) also this contains a basical form of
encryption to make difficult a basical deadlist analysis.
In each of these executable the decryption is implemented in the same way:
Decrypt(String);
It's not necessary to spent many work about that algorithm, cause is a Reducted
Range form of Substitution Cipher.
After building syslcznp.exe, some Registry Key is created and finally
syslcznp.exe executed.
syslcznp.exe
Trojan.Win32.Dialer.qi
Name: syslcznp.exe
MD5: 1CA2A0C7859D1BD3A4DDC5C3491F9036
SHA-1: F03A0E4FBD4FAA457EBF85F70496BBE51A015BD0
This malcious executable is created by Download3.exe and mantains the same kind
of encryption and architecture of previous malicious application. With the
difference that this time, the Dialer opens some Thread and works with Mutexes.
Let's list the Registry Key Operations:
RegOpenKeyExA (HKLM\System\CurrentControlSet\Services\Winsock2\Parameters)
RegOpenKeyExA (HKLM\SOFTWARE\Microsoft\CTF\Compatibility\syslcznp.exe)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\Zones\2,(null))
RegCreateKeyExA
(HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\AppPaths\IEXPLORE.EXE,(null))
As every dialer, it accesses surely some URL, let's list it:
hxxp://www.casinoatropez.com/trcpromo-demetrius-profile-pmail18
hxxp://www.casinoatropez.com/trcpromo-demetrius-profile-pmail18
Strings:
This is the Advisory that appeears AFTER that the connection is enstablished:
Questo servizio vietato ai minori di anni 18
offerto da SmartAdv Ltd e consiste in un accesso per un'ora ad un sito con video
e foto divertenti da scaricare. Per uscire clicca qui.. Cliccando su ok sarai
connesso ad un numero a valore aggiunto al costo unico di quindici euro per
un'ora di abbonamento. Premendo Ok accetti le condizione appena descritte. Premi
OK per proseguire! Buon Divertimento!!!
qui..
Complimenti! Hai abilitato l'accesso all'area riservata. Per entrare clicca su
HappyContent. Per uscire clicca qui.. Offerta: per estendere di altre 24 ore
l'accesso clicca su ok al costo di quindici euro. Verrai anche collegato ad una
connessione di trecento eurocent al minuto. Buon divertimento!
Qui..
Tel Numbers: 899399370,,,01625600000224
899399371,,,02625600000224
password: N00000224
Mef.exe
Name: mef.exe
MD5: 457B534D1141F8B70548506D0D83B4C0
SHA-1: 5D9E106F4B8684D56EF67EB744FCF7CC24B1A23C
mef.exe is a dialer written in VC++ that works with RASAPI32.dll, so we can
suddenly identify it as a dialer. Let's see the Registry Key Activity:
RegOpenKeyExA (HKLM\System\CurrentControlSet\Services\WinSock2\Parameters)
RegOpenKeyExA (HKLM\System\CurrentControlSet\Services\Winsock2\Parameters)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\2mug.biz\,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\2mug.biz\www,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\ZoneMap\Domains\2mug.biz\www,REG_DWORD)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\Zones\2,REG_SZ)
RegCreateKeyExA (HKCU\Software\Microsoft\Windows\CurrentVersion\Internet
Settings\Zones\2,REG_DWORD)
RegOpenKeyExA (HKCU\Software\Microsoft\Internet Explorer\Main)
RegSetValueExA (Start Page)
RegCreateKeyExA (HKLM\Software\Microsoft\Tracing,(null))
RegOpenKeyExA (HKLM\Software\Microsoft\Tracing\RASAPI32)
RegOpenKeyExA (HKLM\Software\Microsoft\Rpc)
RegOpenKeyExA
(HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellCompatibility\Applications\
mef.exe)
RegOpenKeyExA
(HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellCompatibility\Objects\
{871C5380-42A0-1069-A2EA-08002B30309D})
The RegKey operations are all devoted to the correct configuration of IE Browser
settings.
Suddenly after the program EntryPoint we notice some intersting string:
899707789,,,11111100002338
899707788,,,22222200002338
899399376,,,33333300002338
899399383,,,44444400002338
and after these strings
00401E05
00401E0A
00401E0F
00401E14
push
push
push
call
offset aPass
; "pass"
offset aN00002338 ; "N00002338"
offset a899451126 ; "899451126"
sub_402624
899Xxx is the Italian Phone Numeration for PayServices
As every dialer surely there is a PayWebSite releated, and this can be
discovered just with a string search: http://www.pornoaccesso.com/rid=340
The Network Analysis
Malicious executables are placed into an USA Server (mug.biz).
When a victim accesses this website, in the homepage is contained an hidden
iframe that points to an Old Exploit of an ActiveX webcam control of Yahoo
Messenger that attempts to execute a malicious application called
loader_base.exe.
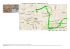
Malware Graph
CartellaUnicaTasse
Download3.exe
Download1.exe
Download2.exe
Mef.exe
pornoaccesso.com
mygalleries.biz
google-hard.com
pornoaccesso.com
syslcznp.exe
casinoatropez.com
Final Words
Finally I want to thanks first of all my Cattina for providing me this malware
example, and Edgar from which I've taken the Hidden Iframe Image! I also thanks
Woodmann, MalwareDomainLists, Tuts4You and Reteam Communities :)